WEB-FORGERY : HOW SAFE WE ARE ON NET
Continuing the legacy of internet security write-ups for Freefeast family, here is the small write-up on Web-Forgery, one more effort from our side to bring this phishing attack into the lights today.
Before starting with web-forgery, I would rather start with forgery, which as per the sources is defined as “The process of making, adapting, or imitating objects, statistics, or documents with the intent to deceive”
The basics remain the same, just the deceiving idea here goes online!
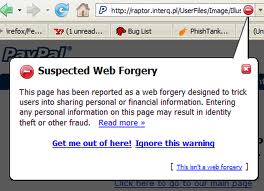
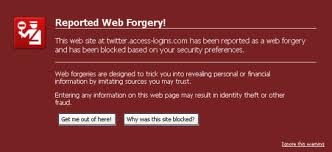
In this,the flaws in the script of actual sites are used for deceiving purpose, wherein the user lands on the original website, and the script which is running on website is manipulated by the hackers by means like placing a picture of a legitimate URL over the address bar, or by closing the original address bar and opening a new one with the legitimate URL.
For Non I.T Visitors: Scripting is the extended programming, which is done for dynamic input/output flow of operations with the users. It is based on the inputs and directions given by users.
Generally it has been observed that “the black hats” play with JavaScript with malicious intentions. It is also called cross-site phishing wherein the users are directed to the original page of a bank or any such entity , hence even the digital signatures are verified and anti-phishing softwares rank it as a genuine site, the problem arises ahead, hackers sometimes use this to perform “Man-in-the-middle” attacks, wherein the attacker makes independent connections with the victims and relays messages between them, making them believe that they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. Such types of attacks are easy when the users are using un-secured wifi network.
The hackers are not only confined to this, when the anti-phishing softwares/plug-ins were thrown in market, which were capable to catch phishing text on the sites, they now use flash based sites, wherein the text is embedded in some form of multimedia content which is skipped by text detectors.
However in this malicious games of “black-hats” we also do have the “white-hats” who are Ethical Hackers and who cater to such types of attacks daily.The technology is advancing and so are they ! Latest updated and upgraded Anti-Phishing softwares / services are smarter than before, and easily catch such practices of hackers.
All we need is the basic knowledge, alert mind-set and frequent updating; we can drive this vehicle called technology very far, ofcourse with a little caution!
Regards,
Deep Bajaj