What is Phishing? | Types of Phishing attacks.Explained by Free Feast
Phishing is a process of procuring confidential information like usernames and passwords by fraud means like sending legitimate e-mails and fooling the unaware users. Mailing systems have evolved in a big way by filtering out spam to an extent. But, it may happen that a legitimate looking e-mail, asking for confidential details like usernames, passwords, social security numbers, address etc.
Surprisingly, they actually manage unaware users to give them their confidential information.Such confidential information is used by the scamsters to use them for wrong means like hacking into their accounts, creating fake accounts or even get loans from banks by providing such confidential details.
For Example: This is a spam email that i received. Anyone would be tempted to give up their personal details after reading this. But, remember me.. “IT IS FAKE“. This is a type of phishing.
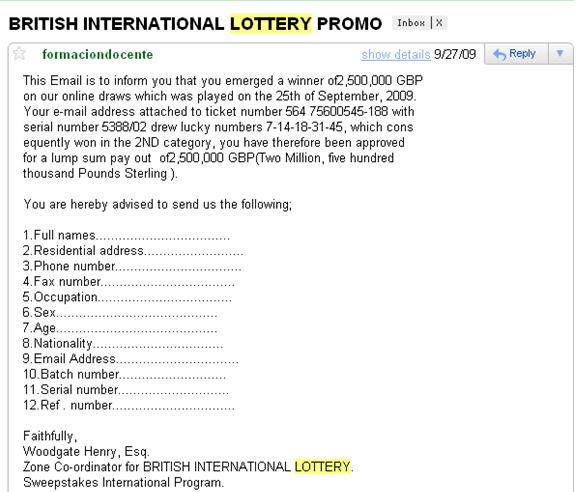
Such emails daily flood our inbox which ask us for our personal details by providing baits like lotteries.The scamsters use such confidential information for creating fake accounts or posing as someone and misusing it.
Following are Four different types of phishing:
1) Phone Phishing (click to know more)
Fraudsters can pose as authorities from a legitimate institution like a bank and phish out details from the users using phone calls.Caller ids can be manipulated using latest technologies and frauds can be easily done.
2) Phishing By Website forgery (click to know more)
This is one of the most common way of phishing. URLs can be redirected using various techniques to a fake website which looks similar like the original. Fraudsters can even make the flaws in such website to their purpose for phishing.
To avoid the anti-phishing techniques, scamsters have started using flash websites in which they hide the text in the flash content.
3) Phishing By Link manipulation (click to know more)
Scamsters create websites with misspelled names of the popular ones.Even if the user accidentally visits them they can still phish out details from the unware users.
Several methods for spoofing links are there . Like using ‘@’ in the link.
Eg: If u type a link like [email protected] you are actually redirected to xyz.com rather than abc.
4) Tabnabbing (click to know more)
This is one of the latest methods for phishing. In this technique the scamsters create exactly a website as one of the popular websites and thereby persuade the user to submit their login details like username and passwords.This attack was discovered and named by Aza Raskin,a security expert.