Advertisement
Asymptotic Notation | Asymptotic Notation in Data Structure
Asymptotic Notation Asymptotic notation is a way of expressing the cost of an algorithm. Goal of Asymptotic notation is to simplify Analysis by getting rid of unneeded information Following are…
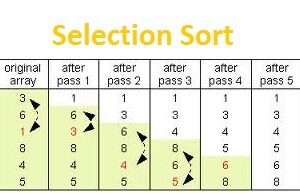
Selection Sort | Pseudo Code of Selection Sort | Selection Sort in Data Structure
Selection Sort follows very simple idea. Let us see what is the idea of Selection Sort : First it finds the smallest element in the array. Exchange that smallest element…
Insertion Sort | Pseudo Code of Insertion Sort | Insertion Sort in Data Structure
Insertion Sort is an efficient algorithm for sorting a small number of elements. It is similar to sort a hand of playing cards. Playing a card is one of the…
CMAT 2014 | CMAT | Common Management Admission Test
CMAT : Common Management Admission Test In India all the proper planning and coordinated development for the technical and management education is handled by AICTE : All India Council for…
Dart Programming Language
Technology is the thing which updates at lightening speed, While talking about programming languages, immediately people name a few as C, C++, Java etc. which are the prominent ones. Today…
Security Suits | Various Anti-viruses
Securing your PC from infection has come a really long way from just protecting it from a simple virus or a worm. A simple anti-virus(AV) program is no longer sufficient…
Windows 8 | Features Of Windows 8
Redmond based software giant is almost ready to launch Windows 8 with the most significant fundamental changes since its Windows 95 days. Metro Rocks Interface for Windows 8 is codenamed…
Acronyms | Diffrent Chat Acronyms | Abbreviations : Part 2
Acronyms Acronym Expansion ATW At The Weekend BRB Be Right Back CM Call Me CU See You CYE Check Your Email DUR? Do You Remember ? F2F Face To Face…
DATABASE HACKING
The database is the heart of any website or application and hacking into it can cause serious losses. First, let us discuss the possible database specific attacks and then talk…
Material For MCA | MCA DOC
Dear Visitors, Here i have added material related to subjects of Master of Computer Applications (MCA). Thanking You. Ms. Poonam Dhanvani MCA Semester 1 Communication Skills - CS : (2610005)…